While movies and television shows never include a scene about jury instructions, in which the attorneys make impassioned (but boring) arguments about comma placement and the definitions of commonly used words, trial attorneys recognize that jury instructions can make or break a case. In a recent employment discrimination trial in Springfield, Illinois, faulty jury instructions may have cost the plaintiff a verdict in her favor, damages in the amount of $100,000, and attorney’s fees for a case that has been litigated since 2011.
The case of Schnitker v. Springfield Urban League ...
Over the past few years, insurance companies have learned that handling liability claims in Missouri with coverage issues or policy-limit settlement demands can be an incredibly complex, and in some cases, dangerous endeavor. Much of that complexity stems from Missouri Revised Statute § 537.065, a statute which has been used as a powerful sword against carriers to collect rather large judgments in many cases.
On April 26, 2017, the Missouri General Assembly voted to repeal the current § 537.065 and replace it with a modified version. That replacement, House Bill 339, was signed into ...

The Local Governmental and Governmental Employees Tort Immunity Act, 745 ILCS 10/1-101, et seq.—commonly known as the Tort Immunity Act—provides certain statutory immunities to local public entities. These protected entities include, but are not limited to, counties, townships, municipalities, school districts, park districts, and other local governmental bodies. See 745 ILCS 10/1-206. The Act sets forth those circumstances in which an entity is entitled to immunity, but many of the Act’s provisions expressly except immunity when an entity’s conduct is ...

Fast food restaurant chain Arby’s Restaurant Group Inc. is known for its great hot roast beef sandwiches and catchy slogan: “We have the Meats!” Arby’s is now communicating a different message; it may be the latest victim of a significant cyber breach.
How are we to digest this? We have grown somewhat immune to the now frequent website notices or press releases that announce that although no one is known to have been harmed, yet another potential information security incident has taken place at yet another company that may have once again exposed customer information.
So what ...

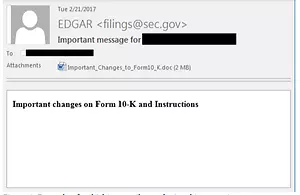
It appears to be innocent and routine. The CFO of your company forwards to you an urgent-sounding, personally addressed email from the Securities Exchange Commission’s EDGAR public filing system announcing changes to the reporting system. Last week you signed the attestation of the accuracy of your Quarterly Report on SEC Form 10-Q. You hope you have not made a mistake or missed an important change. You look over the email again. At first glance it appears legit:
Or it might be your worst nightmare: an email from the SEC questioning your firm’s disclosures, revenue recognition ...

Does your company monitor its network or devices for network security or data confidentiality? Does your company have any policies or practices that seek access to any employees’ personal online accounts? If so, a recent amendment to Illinois’ Right to Privacy in the Workplace Act (“Act”) may require your company to adopt or revise its policies or practices to comply with the law.
Expands the scope of protected content. The amendment has shifted the focus from social networking accounts or profiles to personal online accounts (POAs). A POA is “an online account, that is ...
In insurance coverage litigation, does an insurance company have to identify and produce documents regarding the company’s handling of prior unrelated claims?
Insurance companies often object to such requests on the grounds that they are irrelevant, overly broad, unduly burdensome, and even protected by a privilege. In the Illinois Appellate Court Fifth District’s recent decision in Zagorski v. Allstate Ins. Co., 2016 IL App (5th) 140056, however, the appellate court rather emphatically held that the insured could seek such discovery, at least under the facts and ...

I remember in drivers’ education class being shown the obligatory scary movie on railroad crossing accidents. After the wreck, one salty old train engineer says to another, looking at the demolished car, “Why don’t they learn, Slim?” “I don’t know, Jim,” the other fellow says, scratching his furrowed brow.
In the information security world, we are past the need for scare tactics. Only an ostrich might be oblivious to the heightened cyber risks these days and their increasing frequency. Nevertheless, periodically you see cautionary reminders of mistakes that are ...

A Meaningful Class Action Defense Tool?
On May 16, 2016 the High Court finally spoke on Spokeo, the long anticipated case involving what injury is necessary to sustain Article III standing in federal court. Some predicted a blow to consumer protection and privacy related class actions in which neither the class representative nor the class as a whole suffered anything but a technical federal statutory violation without real harm.
In the underlying case, Thomas Robins claimed that Spokeo published false information about him on its search engine site, in violation of his rights under ...

Unleashing a Trade Secret Misappropriation Federal Private Right of Action
President Obama is poised to sign a bill passed unanimously by the Senate and House Judiciary Committee. What issue of the day could possibly secure such bipartisan support in a tumultuous presidential election year? One that even Donald Trump and Bernie Sanders could agree upon.
The emergence of relatively anonymous cyber threats and persistent state-sponsored economic espionage, together with breaches of confidence and traditional bribery, corrupt employee, and misrepresentation schemes, simply ...